A little help to get you started
Download and use these report templates, methodologies and compliance packages to be productive from day one.
Report templates
Excel - Blank Template
Use this blank Excel report template as a starting point, then populate the "auto" tab with your custom functions.
References
Custom Excel ReportsPublished by: Security Roots Ltd.
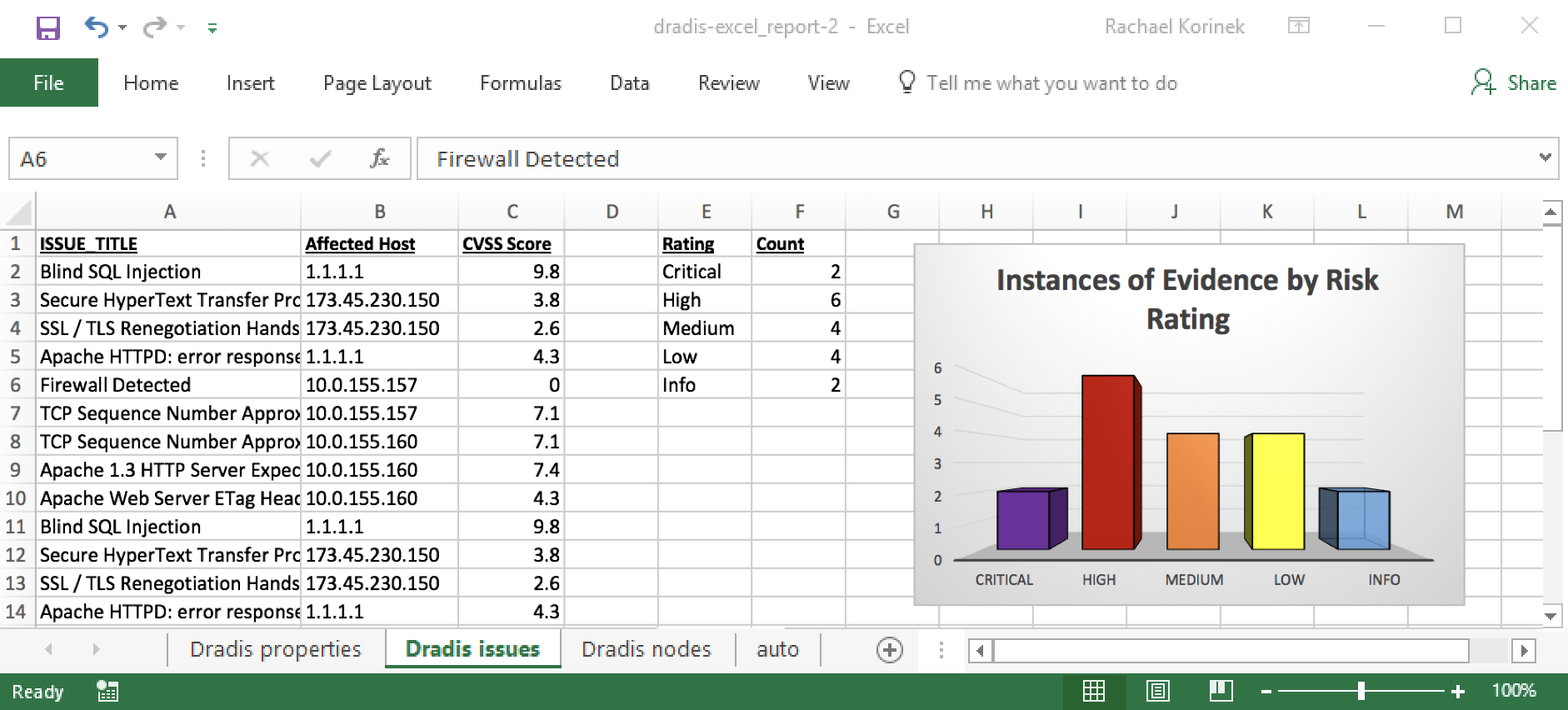
Excel - Simple Template
Custom Excel report organized by CVSSv3 base score, complete with a bar chart showing the number of issues by risk rating.
References
Custom Excel ReportsPublished by: Security Roots Ltd.
Gateway Theme - Ares
Bundled Gateway theme. Use this as a starting point when customizing your team's Gateway layout.
References
Gateway ThemesPublished by: Security Roots Ltd.
Gateway Theme - Atlantia
Bundled Gateway theme. Use this as a starting point when customizing your team's Gateway layout.
References
Gateway ThemesPublished by: Security Roots Ltd.
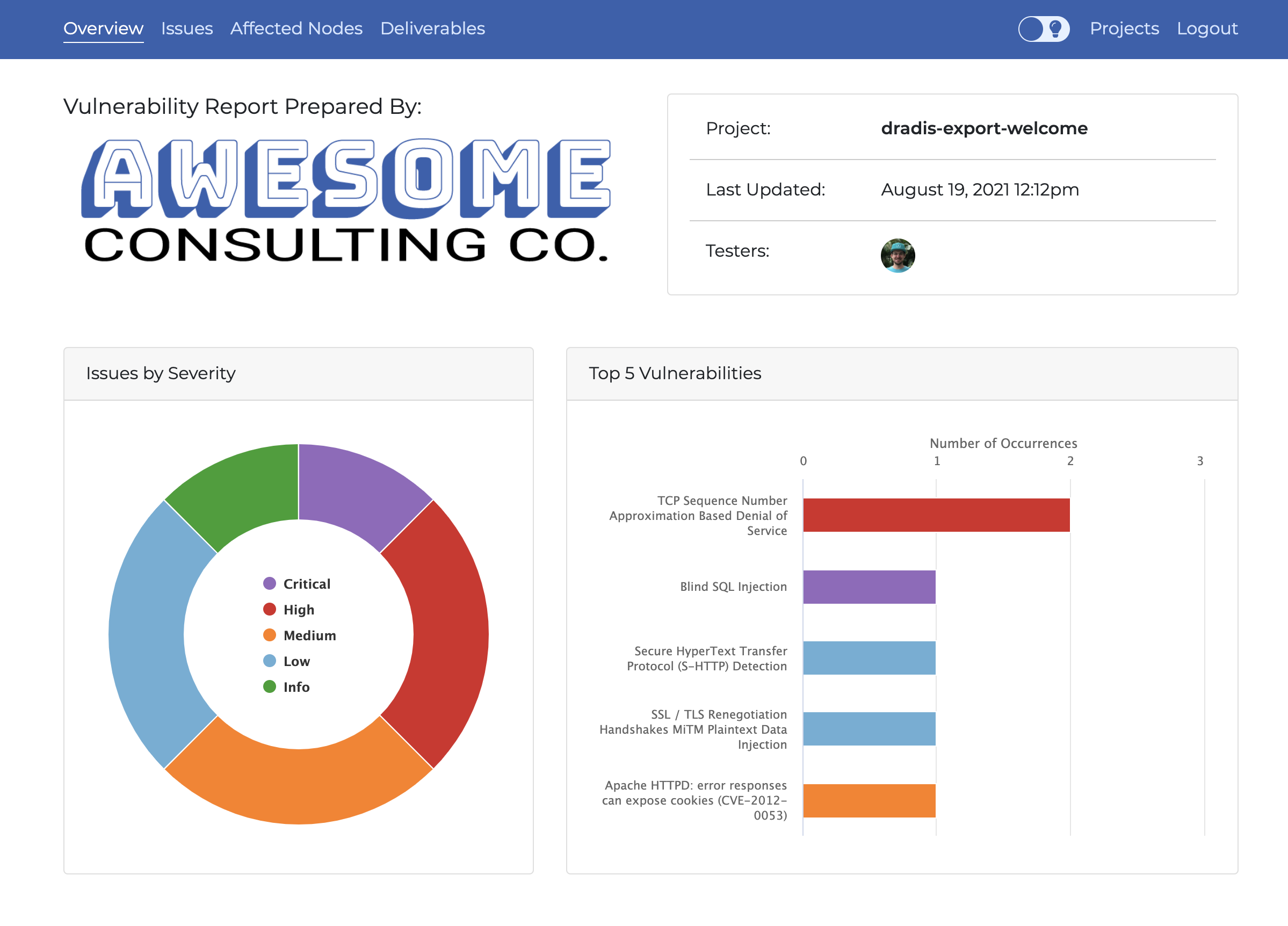
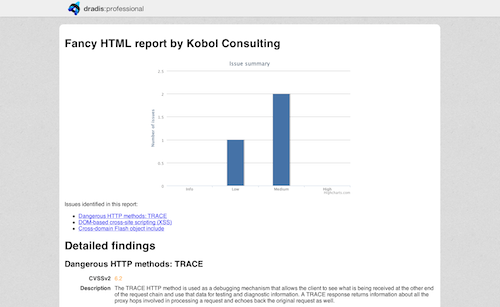
HTML - A fancy report
Not everything is Word! You can create comprehensive HTML reports with charts and detailed issue descriptions.
Resources
Creating HTML reportsPublished by: Security Roots Ltd.
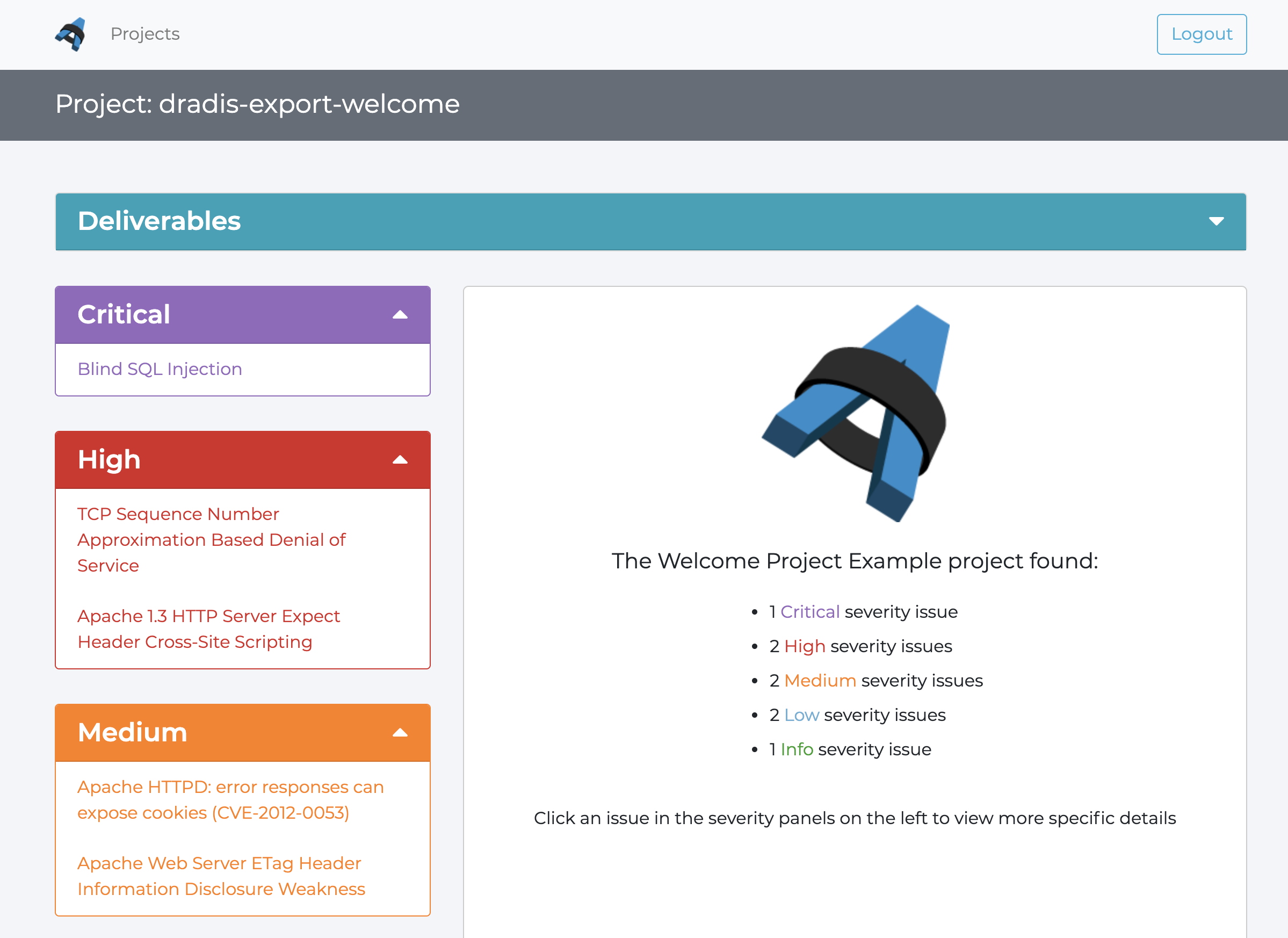
Welcome Kit
A kit with sample templates and a sample project to try out Dradis' functionality.
References
The Welcome KitPublished by: Security Roots Ltd.
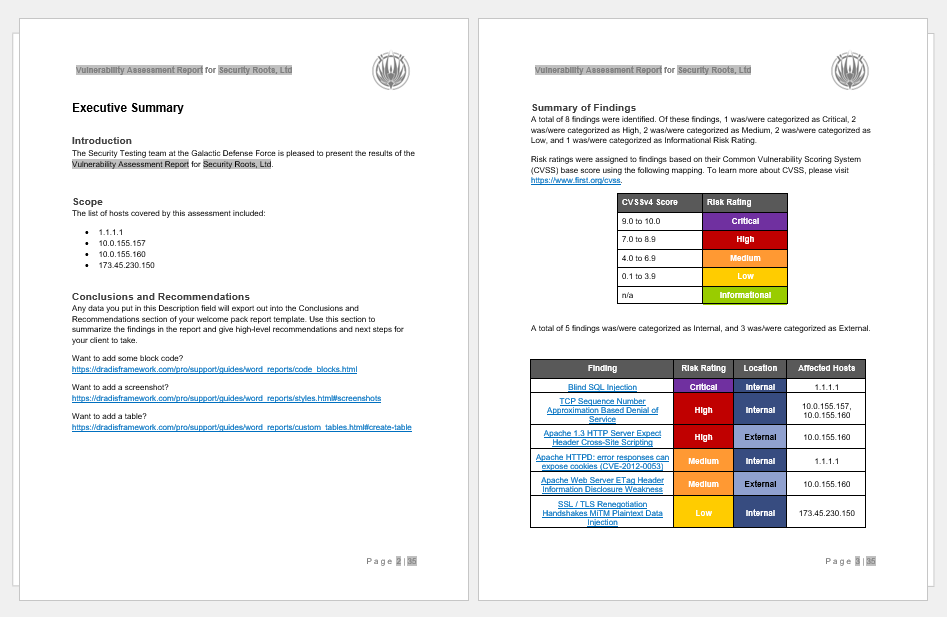
Word - Advanced example
Use Dradis notes for your conclusions, sort your findings by severity, make use of document properties for things like project and client name, etc.
References
Advanced reporting: filters, groups and properties (video)Published by: Security Roots Ltd.

Word - A simple report
A really simple, "no frills" report template that covers the basic reporting capabilities.
References
Creating Word reports with DradisReports (video)Published by: Security Roots Ltd.
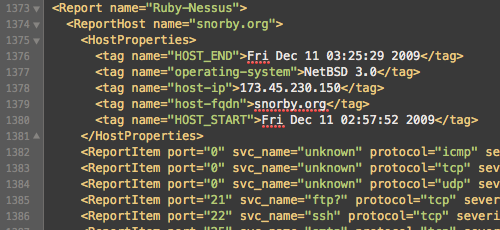
Word - From Nessus to Word: a hands-on-example
Start from a Nessus XML output file and convert it into a custom Word document with whatever branding you want.
References
From Nessus to Word: a hands-on-examplePublished by: Security Roots Ltd.
Word - Grouping and filtering
Learn how to group your issues and filter and sort them by priority.
References
DradisReports: note filtering and groupingPublished by: Security Roots Ltd.

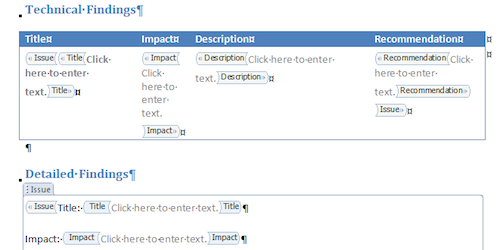
Word - Reporting by host, reporting by issue
Learn how to create reports where you not only provide a list of findings but also a list of which findings affect what hosts and the evidence associated with each instance.
References
Reporting by host, reporting by issuePublished by: Security Roots Ltd.
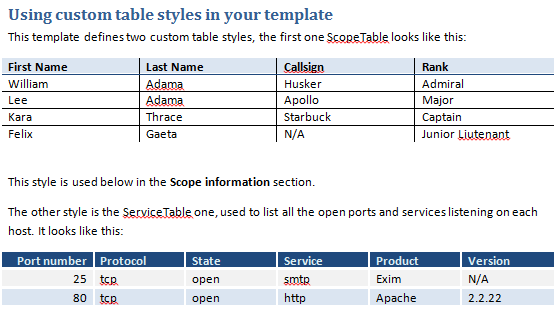
Word - Tables with custom styles
Learn how to create custom table styles for your reports.
Export your Dradis tables into beautiful Word tables.
References
Tables with custom styles guidePublished by: Security Roots Ltd.
Compliance package
HIPAA Compliance Audit Protocol
The OCR HIPAA Audit program analyzes processes, controls, and policies of selected covered entities pursuant to the HITECH Act audit mandate.
Reference
HIPAA Compliance Audit Protocol details
Published by: Security Roots Ltd.

Offensive Security Certified Professional (OSCP) Report
The OSCP examination consists of a virtual network containing targets of varying configurations and operating systems.
Reference
OSCP compliance package details
Published by: Security Roots Ltd.

Penetration Testing Execution Standard (PTES)
It is a standard designed to provide businesses and security service providers with a common language and scope for performing penetration testing.
References
PTES compliance package details
Published by: Security Roots Ltd.

The OWASP Testing Guide v4
The OWASP testing guide is one of the most commonly used standards for web application penetration testing and testing software throughout the development life cycle.
The testing framework was created to help people understand how, where, when, why, and where to test web applications.
References
The OWASP Testing Guide v4 compliance package details
OWASP Testing Guide official site
Published by: Security Roots Ltd.

Testing methodology
OSSTMM v3
Follow the Open Source Security Testing Methodology Manual in your projects.
Reference
OSSTMMPublished by: Kevin Stagat

OWASP ASVS
The primary aim of the OWASP Application Security Verification Standard (ASVS) Project is to provide an open application security standard for web apps and web services of all types.
The standard provides a basis for designing, building, and testing technical application security controls, including architectural concerns, secure development lifecycle, threat modelling, agile security including continuous integration / deployment, serverless, and configuration concerns.
References
OWASP ASVSPublished by: Security Roots Ltd.

OWASP Mobile Security Testing Guide
Follow the OWASP Mobile Security Testing Guide in your projects.
Reference
OWASP Mobile Security Testing GuidePublished by: Security Roots Ltd.

OWASP Top 10 - 2017
Featuring the latest OWASP Top 10 release candidate list.
References
Vojtech Ruzicka: OWASP Top Ten 2017
StackPath: OWASP TOP 10 2017 IS HERE!
Published by: Security Roots Ltd.
OWASP Top 10 - 2021
Featuring the 2021 OWASP Top 10 in methodology template form
References
Published by: Security Roots Ltd.

OWASP Top 10 - 2025
Featuring the 2025 OWASP Top 10 in methodology template form.
References
Published by: Security Roots Ltd.

OWASP Web Testing
A bit of everything, from information gathering to card payments and HTML 5.
References
OWASP: Web Application Security Testing Cheat SheetPublished by: ScotSTS
SANS SWAT Checklist
The SWAT Checklist from SANS Securing the App is meant to be the first step toward building a base of secure knowledge around web application security.
References
Securing Web Application Technologies [SWAT] Checklist SANS SWAT poster (.pdf)Published by: Security Roots Ltd.

Web Application Hacker's Handbook Checklist
Straight from the webapp security bible, this is a checklist of the tasks you typically need to perform when carrying out a comprehensive attack against a web application.
References
The Web Application Hacker's Handbook websitePublished by: Security Roots Ltd.
